The mobile phone has become a necessity in our daily life. All our work be it personal or professional is done with mobile phones these days. From surfing on the internet, having chats with our friends, family, and colleagues to sharing important documents with them, mobile phones and the internet in it, have become an integral part of our lives. Internet is one such interesting thing that lets any two people connect within seconds. When we use web browsers, so many times we get encountered with some errors like Net::err_cleartext_not_permitted. It can be a technical error from the server site or it can be an error due to our low bandwidth.
But have we often pay any notice to those error messages? What can they mean? Or why do they occur? These thoughts rarely come across our minds. We just focus on solving the errors and working on our things. We never try to learn the meanings of those error messages or what message they are trying to give us. One such error message is net::err_cleartext_not_permitted.
How is the development of your app coming along? Do you get a notice that says “net::err cleartext not permitted” when you try to access the website? The good news is that this post provides four effective solutions to the problem you are experiencing with Android Webview. In the next section, we will discuss what this mistake signifies and how you can fix the underlying issue. Keep reading below for some helpful background information, potential reasons for this problem, and potential remedies.

Do not miss: NET::ERR_CERT_WEAK_SIGNATURE_ALGORITHM
What exactly is this Android Webview thing?
Android is a popular mobile operating system with 87 percent of the worldwide market share for operating systems used on mobile devices. Because of this, apps developed for Android have the potential to appeal to a far wider audience than those designed for Apple. In addition, getting an app authorized on Apple’s App Store is far more complex than getting it approved on Google Play. Because of this factor, many application developers have chosen to concentrate on Android development.
The Android WebView is a view that application developers use so that they may include functioning web information in their software. Although the Android WebView is not a very interesting component, it is an essential tool in the Android development process. WebView for Android may now be updated independently of Android itself, and Google strongly advises that all users update their WebViews whenever new versions are released. Any extensive outages or update difficulties will be encountered on applications designed to utilize Webview, which is one of the drawbacks of using Webview. Users who want to avoid experiencing any security vulnerabilities should ensure that their Android operating system is always up to date since fixes are no longer being distributed for Android versions lower than 4.3.
Outside of using a web browser, the only way to see material from the internet on an Android phone is to use the Webview application. A developer may incorporate Webview into an application to control and monitor every user activity inside the program. When a user hits a link inside an application, the site will be loaded within the program rather than appearing in a pop-up web browser when the link is clicked.
What does net::err_cleartext_not_permitted mean?
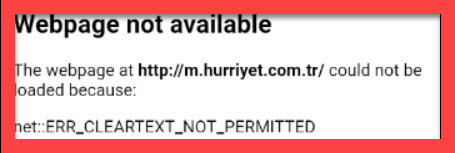
We open so many URLs in our browser. In the android application, Android WebView is used to open these URLs. It is a system component to display contents on the web which is powered by Chrome. WebView is used to display contents on the web of a native application from an embedded browser. We can use WebView to see the content of a link inside any application. Also, we do not need to leave the application. Plus, we can see the contents of it, inside the application. While opening the URLs, sometimes, we get encountered with the error message “net::err_cleartext_not_permitted ”. So, what does this mean?
Any information that is transmitted or stored without encryption is known as cleartext. It is information transferred in an insecure URL. Cleartext Network Traffic raises concern about eavesdropping and content tampering when applications use it to communicate with servers by any third party. User data and information could get leaked by them by injecting any unauthorized data. Cleartext usually uses HTTP URL which is not secure, so risk factors are there while using HTTP. Https is a safer option for secure traffic. From Android 9, the cleartext facility, by default, is disabled. Any application which uses Android WebView to open URLs without HTTPS will throw an error as – “net::err_cleartext_not_permitted”.
Any information that has not been encrypted is referred to as cleartext. As a consequence of this, it is not necessary to decrypt the data to read it. Cleartext is not the same as plaintext, which refers to language in its most basic form and may or may not have been encrypted at some time. Malevolent actors can access information that is sent over the internet in cleartext. The information in cleartext is vulnerable to being stolen or modified.
Google has decided to suppress cleartext information by default to avoid tampering and other malicious behavior, mainly when cleartext data interacts with servers hosted by third parties. This modification was sent out to Android 9 by Google (API 28).
Please note that Android 9 Pie was downloaded on August 6th, 2018. The 11th version of the Android operating system is now available (API 30).
Cleartext messages are almost always sent via an HTTP (hypertext transfer protocol) URL. The error net::err cleartext not permitted will be thrown if an application using Android Webview does not utilize HTTPS after the Android 9 release. All apps utilizing Android Webview are required to use HTTPS. Users of your application may see this error while visiting HTTP URLs because of the way Android’s network security setup is set up.
Why does this error keep coning up
We know the meaning of net::err_cleartext_not_permitted error. Now let us know Why does this error keep coning up. The reason for this error is the fact that cleartext support has been disabled in your device due to security purposes. So, when we try to open a website with an HTTP URL in Android WebView, this error occurs to let you know that WebView cannot access that website due to security reasons. The website that you are trying to open may be prone to attacks and can be hacked easily so this error does not let you access that unsafe website.
How to fix net::err_cleartext_not_permitted?
The most convenient and easy way to fix the “net::err_cleartext_not_permitted” error is to use URLs with HTTPS. We should not use insecure URLs and use a website with an HTTPS URL. We should remove all insecure non-HTTPS URLs from our applications. Developers can force HTTPS for websites but they must be having a valid SSL certificate for their domain. There are few ways to do it are:
- We must log in to the File transfer protocol or cPanel.
- Go to File Manager.
- In the root directory, generate .htaccess.
- Write the codes to the .htaccess file. Save the file.
- The PHP config file must be edited. The site and base URL must be updated.
Any application developer, facing the issue of “net::err_cleartext_not_permitted” can fix it by adding some code to the AndroidManifest.xml file. The code is android:usesCleartextTraffic= “true”. The developer needs to add this code in the AndroidManifest.xml file. After the code is added the flag starts to accept non-HTTPS traffic and the error is fixed.
Programmers may remedy the Android Webview problem known as net::err cleartext not permitted by restricting their applications to accept only HTTPS URLs. HTTPS connections may be made to any website with a current and active SSL certificate. As a result, you need to eliminate any insecure URLs and make HTTPS the default for all websites.
You will first get familiar with a quick workaround before moving on to methods that will compel HTTPS. If you are unable to force all connections, you have the option of selecting this one instead:
Edit AndroidManifest.xml
An AndroidManifest.xml file will be present in every Android application. This file includes essential information on your application, such as the activities and services it provides. AndroidManifest.xml is the file that not only specifies the application’s Android API but also gives permissions for any areas of the program that are password protected.
You will change the application subelement immediately (within the manifest). You are going to be adding a simple application tag.
Caution: This workaround should only be used as a temporary patch. Doing so will jeopardize the data integrity of your users owing to the significant risk presented by cleartext data transmitted through HTTP URLs.
The following is an explanation of how to change the AndroidManifes.xml file:
- AndroidManifest.xml may be found in the application folder at the following location: android/app/src/main/AndroidManifest.xml.
- Find the application subelement using the search bar.
- Include the following tag in your post:
- android:usesCleartextTraffic=”true”
- The following format should now be used for the application subelement:
<application
android:name=”io.flutter.app.Test"
android:label=”bell_ui”
android:icon=”@mapmap/ic_launcher”
android:usesCleartextTraffic=”true”>
- The AndroidManifest.xml file should be saved.
The following two techniques will include requiring HTTPS on websites that are either built using WordPress or using HTML/PHP. Suppose you are developing an Android application to complement a web application (there are many reasons to make a native app). In that case, you should expect a significant amount of URL overlap. There are several advantages to developing a native app. As long as an SSL certificate is present on your server, you can update your website to require visitors to use HTTPS instead of HTTP.
Make all WordPress sites use HTTPS by Default.
You will need to change the—access file to make HTTPS the default protocol for a WordPress site. The .htaccess file is used to manage permalinks and redirects on the website.
- Log in to the WordPress site’s admin dashboard.
- From the left-hand dashboard, go to the Settings menu and choose General.
- Find the address (URL) of WordPress and the site’s address (URL), and check to see that both of these addresses use HTTPS. To do this, your website will need an SSL certificate.
- To change the files that makeup WordPress, you will need access to a file manager, which may be obtained via cPanel or FTP. Different choices, such as plugins, may also provide this capability to the user. Find the .htaccess file that is contained inside the root folder, and then open that file.
- Find the # BEGIN WordPress instruction inside this code. This is the beginning of the WordPress guidelines you will modify in the future. This whole section, which now ends with # END WordPress, should have the following content replaced with it. Make careful to change the XXXX with the name of your domain, but refrain from reorganizing the content in any other way:
# BEGIN WordPress
<IfModule mod_rewrite.c>
RewriteEngine On
RewriteBase /
RewriteRule ^index\.php$ – [L]
# Rewrite HTTP to HTTPS
RewriteCond %{SERVER_PORT} 80
RewriteRule ^(.*)$ https://XXXX.com/$1 [R=301,L]
RewriteCond %{REQUEST_FILENAME} !-f
RewriteCond %{REQUEST_FILENAME} !-d
RewriteRule. /index.php [L]
</IfModule>
# END WordPress
Make sure that the .htaccess file has been updated with your modifications.
Make HTML and PHP Websites Use HTTPS Only
- Launch either FTP or cPanel and go to the directory that serves as the site’s root.
- If you are currently logged into cPanel, you may add a new file by clicking the “+ File” button on the toolbar at the top. When using FTP, you may right-click anywhere within the root directory to get the menu that allows you to create a new file. Make a file and save it with the name.htaccess.
- Launch the.htaccess file that was just generated in the root directory.
- If your website utilizes a www address, then you need to add the following block of code to the.htaccess file of your website:
RewriteEngine On
RewriteCond %{HTTPS} !on
RewriteRule (.*) https://%{HTTP_HOST}%{REQUEST_URI} [L,R=301]
RewriteCond %{HTTP_HOST} !^www\. [NC]
RewriteRule .* https://www.%{HTTP_HOST}%{REQUEST_URI} [L,R=301]
If your website uses a URL that does not begin with “www,” you need to add the following code block to yours .htaccess file:
RewriteEngine On
RewriteCond %{HTTPS} !on
RewriteRule (.*) https://%{HTTP_HOST}%{REQUEST_URI} [L,R=301]
RewriteCond %{HTTP_HOST} ^(www\.)(.+) [OR]
RewriteCond %{HTTPS} off
RewriteCond %{HTTP_HOST} ^(www\.)?(.+)
RewriteRule ^ https://%2%{REQUEST_URI} [R=301,L]
If your website runs on PHP, you will also need to edit the PHP configuration file, the URL of your website, and the variables used in base URLs.
Modify the file called “network security config.xmi.”
The subsequent solution is accessible for use by apps that are running Android version 7 or later. Developers may edit the network security configuration in the network security config.xml to fit their specific application’s requirements. You can update this file to exempt a particular domain name from security constraints. The net::err cleartext not permitted error will not be triggered by network communication employing this domain.
- Place a file with the name network security config.xml within the program folder for your Android device, and save it in the following location: res/xml/
- Insert the following text into the domain configuration. Make sure that the portion that says your domain.com is changed to the URL of your website.
<?xml version=”1.0″ encoding=”utf-8″?>
<network-security-config>
<domain-config cleartextTrafficPermitted=”true”>
<domain includeSubdomains=”true”>your_domain.com</domain>
</domain-config>
</network-security-config>
- Ensure that the network security config.xml file is updated with the modifications.
- AndroidManifest.xml may be found in the application folder at the following location: android/app/src/main/AndroidManifest.xml.
- Find the application subelement using the search bar.
Android Webview problem categorized as net::err cleartext not permitted resolved
Any Android developer worth their salt should have at least one copy of the Android Webview application in their toolset. Within a native application, the developer can show online content such as their own or a third-party website using the Webview component. If Webview is not utilized, the only technique to deliver web content requires a break in the normal flow of the application’s operation. A browser, another piece of software, will launch when this button clicks. Once a user leaves your application, there is a possibility that they may
never come back. This may result in a decrease in sales, traffic, and advertising income.
If you had implemented the methods presented before, you would have modified the AndroidManifest.xml file associated with your application to include an exception for cleartext communication. You have generated and changed a file named network security config.xml to allow a specific domain for cleartext network traffic.
The second and third options are beneficial if you are constructing a web application for an application with considerable URL overlap.
- You have learned how to compel the usage of HTTPS for a web application that is either built using WordPress or HTML/PHP. cPanel or File Transfer Protocol (FTP) must be used to change the .htaccess file.
- So here, you can accomplish so here if you would like to get further knowledge about the setting of Android Network Security, especially cleartext traffic rules.
- You can do so here if you are interested in gaining further knowledge about Android Webview. Studying the documentation will give you a better grasp of Android Webview since the material is quite good. From what was just said, you are aware that using Webview is not without limitations.
During the process of constructing your app, you could potentially come across issues relating to Android WebView. However, you do not need to be concerned about this matter since we have already discussed the second typical WebView error message, erring an unknown URL scheme, in a different post.
Facebook:
Facebook has become a very popular and biggest social networking site. People from all over the world can connect through Facebook. Facebook helps people to socialize and makes its revenue from advertisements. The users of Facebook have to create an account using a valid email-id or phone number followed by a password. Users can write about their personal feelings, add photos or videos and connect with people around the world. People have been so addicted to Facebook that they post every little information about themselves on it. They click on anything that appears on their feeds. They search for people and make connections with strangers within that platform. Facebook has become an integral part of social networking.
net::err_cleartext_not_permitted in Facebook:
But sometimes, when we are clicking on any article or a link in the newsfeed of Facebook, we get to encounter an error as- net::err_cleartext_not_permitted. This error means that the application does not allow you to open articles or links with an HTTP URL. The said article or link may connect you to an insecure website that may be prone to hacking attacks or any other security concern. This feature has been a major update on Facebook. There have been many incidents when hackers have attacked and hacked the accounts of users using these links on articles. The danger online is no joke now. People lose their hard-earned money and reputation while committing some silly mistakes online. These updates are made to make people aware and careful about malicious activities that can happen through links to insecure websites.
Facebook Messenger
Facebook Messenger, a messaging app created by Facebook is now prone to hacking attacks too. The application was created as an instant messaging platform. The vulnerability in this application lies in the fact that any user who visits the website using insecure links from Messenger, while still being logged in to Facebook, can give their personal information to attackers. The information can include the name, email address, contact, educational qualification, place of living, interests, and hobbies of the user. The messages in Messenger are not encrypted end-to-end which makes it more vulnerable.
Hackers
Hackers can easily access your Messenger and know the people you are contacting and messaging. Also, hackers make use of this platform to spread insecure links. These links can turn into a huge cyber threat when they are clicked. Hackers send dummy messages with text, video, or audio attached with a link. These links when clicked, direct users to malicious websites on their browser. The hackers can even infect the user’s device.
If the user’s device gets compromised then the hackers make use of it to send malicious links to the contacts of that user. The cycle continues and more devices start to get infected in a chain reaction. If the attack is more serious, then the hacker can track the keyboard activity on the device which can reveal the bank details of the user if he regularly uses banking applications. The hacker can easily make use of the details and can cause bigger harm to the user.
In some cases, links that appear to open a YouTube video are sent to users on Messenger. These links are also available as an advertisement in the newsfeed of the users. It seems that when you open this link, you will be able to watch a YouTube video. When you open the link, it does not take you to any video but a fake, Facebook Login Page. Many users find nothing wrong with these links and at once log in with their credentials. Users cannot differentiate between the real and fake pages and end up giving their credentials.
Block any unauthorized access
Attackers can easily use their credentials and hack their accounts. They can use the hacked account to perform any malicious activity. He can further forward the link to people on your friend list. We must always take care while clicking on any links on Facebook. Further, we must not click on any link which might be suspicious.
Here net::err_cleartext_not_permitted comes to play. Since cleartext is disabled by default in most of the devices having android version 9 and above, any link with unencrypted information will not open and the error message will get displayed to the users. This is an important step to conserve the user information and block any unauthorized access to the user’s device via any links.
Learn more about com.facebook.orca & com.facebook.katana.
Summary:
There are even links on Facebook that seems to open a YouTube video but will redirect you to a fake Facebook login page. The attackers can get user credentials from it and do malicious activity on the user account. net::err_cleartext_not_permitted error does not let the users open any insecure website using an HTTP URL. Thus the users are saved from any malicious activity conducted from insecure links and websites.
Here, I will offer a simple method to repair the err cleartext not permitted problem, and that is to avoid using URLs that are not secure. It is strongly suggested that you switch all of your websites over to HTTPS and delete all URLs that do not use HTTPS from the application. The following tutorials will be of use to you in the process of imposing HTTPS on your websites.
Frequently Asked Questions
If you want the link to open in a new window, you can also alter the URL href code and add the target=” blank” attribute. This is a more roundabout solution. Adding new intents with URL schemes is another option to cure the mistake. Objectives tell the Android device what the users want for the program to perform; therefore, adding new intents with URL schemes is a way to correct the error.
If you need your application to be able to load plain http:// URLs, you have the option of enabling cleartext traffic by using an AndroidManifest. xml file that contains the android:usesCleartextTraffic=”true” application attribute. This is only necessary if your application is required to support loading plain http:// URLs.
The correct way to fix this problem is to use HTTPS URLs for all your endpoints and delete unsecured URLs from your codebase. This is the only alternative that will be successful.

I am Ajanta Chettri. I am an easy-going, ambitious, joyful girl from Kalimpong in West Bengal. Have extensive expertise of Android, iOS-based tech bugs. In my free time, I like to read books, listen to music, and explore tech things. I love to indulge in technical writing content. I have a personal blog where I write thoughtful short poems and stories. I am passionate to do my work and I stay optimistic and motivated whenever I sign up for anything. I try to learn from the mistakes.