The dark web has long been a topic of intrigue, made even more mysterious by Hollywood impressions and scandals such as Silk Road. For most folks, the image of a Snowden-type hacker in a dark hoodie, dark shades, or with an anonymous-type mask is immediately conjured up when one mentions the Dark Web.
We’re here to give you a quick tour of the deep and dark web, explain why it remains hidden from prying eyes, and debunk all the myths about it. Hopefully, you’ll learn something valuable especially if you are a student or a programming enthusiast.
Let’s dive in.
The Origins of the Dark Web
The concept of the Dark Web began with the development of The Onion Router (TOR) in the 1990s. Initially created by the US Naval Research Laboratory for secure communications, it eventually found civilian use, allowing people to navigate the web anonymously. Thus, the original Dark Web was born.

The Dark Web functions to provide anonymity, privacy, and, the ability to stay anonymous. Dark Web sites usually have a .onion URL. Thus, on the dark web, you’ll find a variety of sites including chatrooms and forums, marketplaces, government agencies, and even newspaper IPs in countries where reading these online resources would be illegal or dangerous.
Debunking the Dark Web
So, is the dark web illegal, and will accessing it land you in jail? Do you need to be a hacker par excellence to access the Dark Web? Is the Dark Web actually dark? Not necessarily. According to a recent study, there were over 65,000 unique .onion sites on the dark web, and most of them serve legal and legit purposes. For example, Facebook is known to maintain dark web sites to facilitate communication in countries with oppressive policies.
On the other hand, there are sites that do exist on the Dark Web whose activities are not entirely legal or ethical. Terbium Labs has cataloged about 200 domains, mostly illegal marketplaces selling all types of drugs, counterfeit documents, and unethical services (hacking, guns for hire, pornography, and counterfeits). A lot of the transactions on these sites are conducted in crypto such as Bitcoin and Ethereum.
Surface Web vs. Deep Web vs. Dark Web
Let’s assume that you’re looking for a “Do my essay for me” website. In this case, you need a ranking of such websites by Google which will then provide the most reliable selection. This is an indexed site that can be found traditionally on Google and other search engines. This website therefore exists on the Surface Web, or Clearnet.
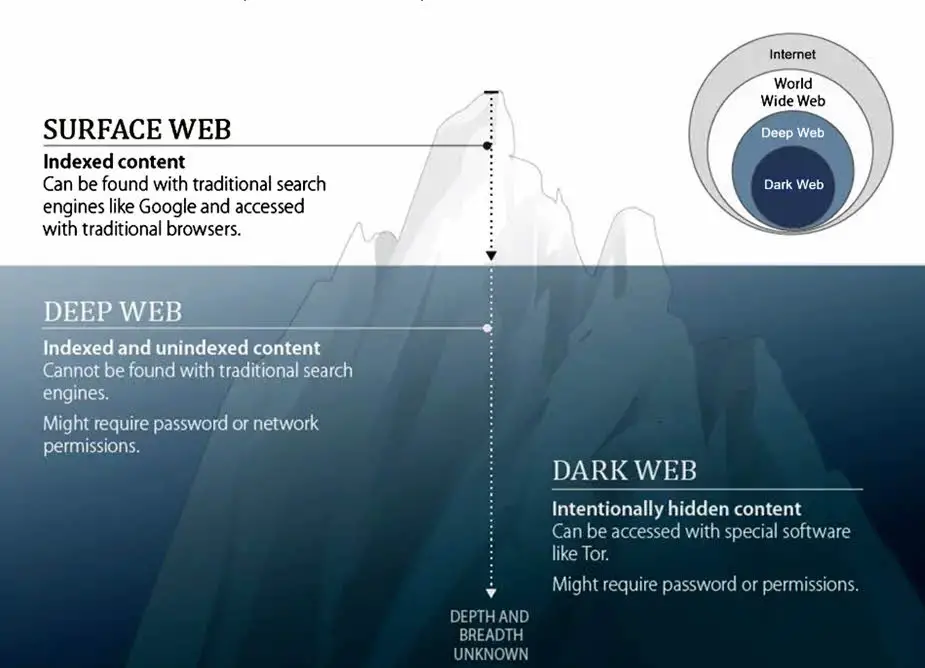
However, let’s assume that you are a security agent working for the CIA on a high-risk project hosted on a remote, external server. The login page for such a project might not be found through a regular URL search on Google. You might require an invite to authenticate your credentials and access such a site. However, you might not necessarily require a .onion URL to access this site. Such a site may therefore exist on the Deep Web.
Now, let’s say you want to access an e-commerce marketplace selling contraband. In this case, you want to remain completely anonymous and untraceable. An option here would be to try to use a VPN to hide your identity, but the illegal site would bounce off any such request. That’s where the Dark Web comes in.
Indexing on the Surface Web
The Surface Web refers to the visible or public web. Here, indexing is an important part of how search engines like Google, Bing, and Yahoo operate.
User ──────── Search Engine ──── Web Crawler ──> Index
Search engines employ web crawlers or spiders to continuously browse the internet by following links from one page to another. The crawler then moves from one page to the other, extracting content such as text and images. The extracted data is then processed and indexed, i.e. structuring the data to facilitate quick and efficient searching.
The search engine searches its index to find a query entered by the user to find web pages that match the query. The search results are then ranked depending on the relevancy of each page and the results displayed.
Indexing on the Deep Web
The Deep Web consists of web pages and content that aren’t indexed by search engines. Content on the Deep Web is intentionally hidden from search engine crawlers. Content can be non-indexed through various means, such as using the “robots.txt” file, requiring login credentials, or employing server-side filters.
User ──> Access Portal (Login, Database Query, etc.) ──> Private Database or Resource
Much of the Deep Web comprises databases and resources like academic databases, subscription-based content, and private networks. These are not indexed but can be accessed through specific portals, ergo, the CIA example provided above. Also, keep in mind that Deep Web sites are accessible on both the Clearnet and the TOR network, which we’ll get to a little later.
Indexing on the Dark Web
The Deep Web and Dark Web essentially run on the same principle of non-indexing. However, the Dark Web has to be accessed through the TOR network.
Websites on the Dark Web have .onion URLs, which are not part of the traditional Domain Name System (DNS). Conventional search engines don’t index these domains. To access these domains, users would need to connect to the TOR network.
User ──── TOR Network ──> .onion Peer-to-Peer Directory
Rather than typical web addresses, .onion addresses appear as lengthy strings of numbers and letters, like this CIA address: (ciadotgov4sjwlzihgdgdgdgg3xiyrg7sosd2o3lt5wz5ypk4sxyjstad.onion)
Such a link won’t lead anywhere on a standard browser.
Accessing or Running a Website on the Dark Web
Let’s say you needed to hire a writer online for your school paper; you’d probably go through a safety protocol first. Likewise, without a proper safety protocol for accessing the Dark Web, you might end up getting hacked, tracked, or your information like email addresses, social security numbers, and credit card info stolen.
Here are a few steps to consider:
1. Download TOR
TOR (The Onion Router) protocol is the basis for staying anonymous on the Dark Web. You can download that from torproject.org. The TOR network allows you to access deep web links which Google or any other standard browser can’t. “Onion” is a ref to the fact that the node-connected network is layered.
You do stay anonymous since the network masks your IP and doesn’t collect or store personal info with cookies. You can even choose a different IP location far from your location, with a different IP protocol. The user initiates a connection to the TOR network which reroutes the traffic through multiple nodes, with each node only aware of the previous and next hop.
2. Connect Your TOR to a VPN
You might be wondering why you still aren’t safe at this point with TOR downloaded. While your IP is masked from the websites that you visit, it isn’t masked from your ISP and neither is it masked from the first onion network you connect to. Thus, you still need an extra layer of security, and a VPN is the way to go.
Let’s take the example of Nord VPN, one of the most reliable VPNs available currently. NordVPN easily connects to onion sites and can also provide app kill switch, high-powered encryption, and DNS leak protection. Before accessing your “illegal” onion site, you’d download and install NordVPN on your PC or Mac.
Once your VPN is ready and you have maxed the security settings, you can now connect to the TOR network. You might also want to change your browser settings back to basic at this point to disable JavaScript, forms, HTML5 media, WebGL, and other scripts.
These two steps (TOR and VPN) might be enough for most sites that aren’t illegal. However, there is an extra layer of security that can be implemented if you need total protection on the dark net.
3. Download Tails Linux
Tails Linux is a portable USB operating system, with a project mission of protecting against tracking, censorship, advertising, and viruses. This is your “burner” computer that ensures that your computer is untraceable by prying eyes, whether websites visited, files downloaded, or passwords used, even with password managers.
First, you’d have to have an extra USB stick, preferably one with good capacity since the Tails file download is about 1.3 GB alone, and the OS needs at least 8GB to install and run. For files, docs, and other downloads, you can also have secure persistent storage encrypted by Tails on your USB stick.
Tails also comes pre-installed with an enhanced TOR u-browser which blocks applications automatically if they are not connected to the TOR network.
Now your Dark Web browsing is secure, and you can check out those “illegal” sites without worrying about the law knocking on your door, or getting totally hacked and decimated.
4. Getting Deep Web Links
Now you’re ready to go “deep cover” on the dark net. However, you need a directory of the onion sites before you can enjoy your experience.
You can find these directories either on the Clearnet or the TOR network. Deepweblinks.live and Ahmia.fi are two of these directories. You can then copy-paste the links onto your TOR browser.
Disclaimer: This article is for informational purposes only and doesn’t endorse illegal activities. While it offers security measures for navigating the Dark Web, no method guarantees full safety. Accessing the Dark Web can lead to potential legal repercussions, data breaches, or exposure to malicious content. The publisher and author disclaim liability for any consequences from using this information. Exercise caution, and consult legal counsel if unsure of any action.
Conclusion
Bravo! You just took a giant leap toward making your Dark Web browsing experience more secure. It’s worth some time and effort, but the result is that you join a very small percentile of people on Earth who’ve actually done this.
Contrary to popular belief, the Dark Web can be a force for good. By following the steps above, you can explore this hidden part of the internet for legitimate purposes.

I am a Bachelor of Technology in Electronics and Communication branch. My technical skills are python, SQL, C language. RightNow I am learning web development. I have also worked for an NGO which I also always wanted to do when I was a kid since at that time, I was inspired by Mother Teresa, so I wrote an article on her from there I started feeling like I like writing. Then as growing up I fought my interest in learning about new technology so I always try to learn about something new on daily basis and write about it. I have always been a hardworking, sincere, and disciplined person which always helps me in every aspect.


