Hello there, welcome back. Today we will be discussing about com.qualcomm.qcrilmsgtunnel. We will try to cover almost every stuff related to it. These include what is com.qualcomm.qcrilmsgtunnel, what is its purpose. We will also take a look into whether or not it is a virus.
In the modern world of technology, we deal with smart devices. The two major components of devices are hardware and software. These two things are interdependent. The software, to run, needs proper hardware. Also without software, hardware has no value. These are same basic things and you might have started getting bored. Let’s straight away talk about processors that power your device.
Now when we talk about Computer processors, the two leading names that come into our mind are Intel and AMD. However, when it comes to smartphones, you can’t deny that the first name that comes to your mind is Qualcomm. Qualcomm is one of the most popular companies that manufacture mobile processors that most of the devices use. The main aspects of Qualcomm processors are:
- Quick Charge Technology, that allows devices to charge up to 4x faster than conventional charging speeds.
- Qualcomm Mobile Security, that safeguards your device from malicious attacks.
- Qualcomm Spectra Camera ISP (Image Signal Processor), which supports the capture of up to 192MP and that too, with no shutter lag.
The Qualcomm Snapdragon processors are some of the fastest mobile processors that the company provides. They are designed for enhanced camera functionality, lag-free gaming experience, better AR and VR experience, extended battery life features, and the latest security solutions. Qualcomm also has designed CloudAI 100 for AI inference acceleration. Some of the featured processor applications are as follows:
- Automotive
- Smart home
- Audio
- Smart Cities
- Wearables
Don’t Miss: com.qualcomm.atfwd
What is com.qualcomm.qcrilmsgtunnel?
Don’t get confused by its long spelled name. com.qualcomm.qcrilmsgtunnel, is a package that is most likely to be found in your device if it is powered by Qualcomm. com.qualcomm.qcrilmsgtunnel is a part of the stock phone dialer for devices powered by Qualcomm processors. It is known to handle RIL / messaging. The included packages are com.qualcomm.qcrilmsgtunnel, SIM Toolkit, Phone or Messaging storage, and Phone.
See also: com.qualcomm.embms
Qualcomm
This term is not new to you. Especially you might have come across this term while buying yourself a new smartphone. Qualcomm is an American multinational company that deals with semiconductor devices. It does not manufacture physical products like smartphones or infrastructure equipments. Software, semiconductor designs, patented intellectual property, are some of the fields where Qualcomm excels in. It is well known for its market share in wireless technologies.
The business is divided into three categories by Qualcomm:
- Qualcomm CDMA Technologies (QCT), that manufactures CDMA wireless products and constitutes 60% of the revenue.
- Qualcomm Technology Licensing (QTL), that does the licensing. It constitutes about 19% of the revenue.
- Qualcomm Strategic Initiatives (QSI), that involves investing in other tech companies. This sector constitutes about 1% of the revenue.
Qualcomm is one of the leading provider of semiconductor products for wireless communications. It has 39% market share for smartphone processors, 50% market share for baseband processors, 18% market share on tablet processors. Not only that, according to ABI Research, it has 65% market share in LTE baseband. It is estimated to earn an amount of $20 for every smartphone sold around the globe. By these huge numbers, you can well imagine how big is the company in this sector.
The reason why I said that you may not be hearing it for the first time even if you’re not a tech freak is that, knowingly or unknowingly you too have come across this. Most probably even the smartphone you’re using right now is powered by a Qualcomm chipset. (Except Realme phones, that are powered by the MediaTek Helio processors).
The Qualcomm Security Breach of 2016
Back in 2016, there arose a new widespread vulnerability in devices with Qualcomm chipset. It affected millions of Android devices around the world. It could allow hackers to read phone records, sensitive data, text messages, and all other things the radio allows.
- To make it worse, there was this fact that the victims would be totally unaware about it. They would have absolutely no idea if they have been hacked. Also, most of the affected devices would not be patched.
- The hack involved netd daemon. Netd daemon was a network interface in Android. Qualcomm released some new APIs which also involved the netd daemon, that allowed additional tethering capabilities.
- The vulnerability was labelled as CVE-2016-2060. Thus, popular cyber security company FireEye worked closely with Qualcomm to release a patch quickly.
- The hacker would most likely exploit you by adding code to a malicious software that you installed. Like this, millions of smartphones could be targeted remotely.
- A malicious application could interact with the Qualcomm-released API without your consent. That is why you would not be alerted or your device would perform flawlessly.
- The good thing is that, only devices running Android 5 or lower having Qualcomm processor was affected. If you still use a device with Android 5 or lower with Qualcomm chipset, it is recommended to upgrade. We have reached Android 11 and as the price of low-range smartphones fall, it is a good choice to upgrade.
- To know the hardware information of your device, you may download CPU-Z app from the Google Play Store. It tells you your device model and processor model in no time. Also, you can go to Settings > About phone. Then find the number (android version). If it is 5.1.x or below and your device has a Qualcomm processor, you’re likely to be infected.
What can you do to be safe?
- Upgrading to a higher Android version is the best choice. Otherwise there is very little to do to be safe from hackers.
- Never download any third party app or app from third party website. Download apps only from Google Play store that are verified by Play Protect. Downloading and installing unknown APKs from third party websites may install malicious softwares in your system. Without your knowing, hackers would be able to steal your data. So, download only popular apps that are highly rated.
- Though it is almost impossible for antivirus programs to detect the vulnerability, it’s good to have antivirus. Install a popular antivirus in your device and go for some premium plans. It would of course protect your device from other threats, viruses and attacks.
Is com.qualcomm.qcrilmsgtunnel a virus?
No, com.qualcomm.qcrilmsgtunnel is not a virus. There is no report saying that some antivirus program claims it to be a virus. In short, It is just a pre built package related to the stock phone dialer of devices powered by Qualcomm chipset.
How to fix com.qualcomm.qcrilmsgtunnel has stopped?
If you face this error, it’s really annoying. Chances are that if this error keeps on popping, you won’t be able to use your device’s dialer or messaging. This is because crashing of this built-in app would cause the systems related to it misbehave. To fix this, you may follow the regular steps as follows.
- Head on to the Settings of your device.
- Locate Apps, and then go to “All Applications” or “Running Apps”.
- Find com.qualcomm.qcrilmsgtunnel from the list of installed and running apps.
- Once it opens, click on “Force stop”. This forcefully stops the app, and now the problem might be fixed.
- Also consider clicking on “Clear data” to clear the cache of the app.
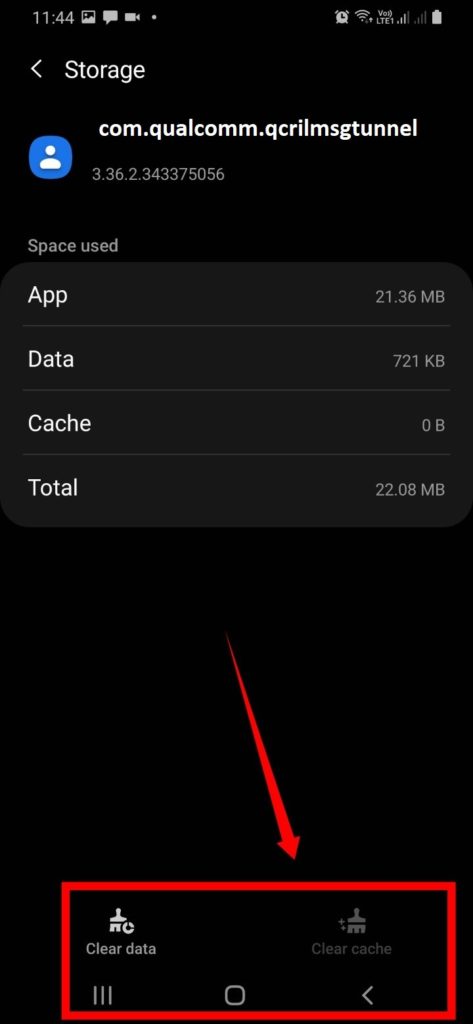
Clearing data is not that important. This is because once the app auto restarts, it will regenerate all that data once again.
If opening the dialer is what causing the app to crash, then try downloading a third party dialer from Google Play Store. Make sure you download a trusted and highly rated dialer. This is obvious because dialers would need permission to your call log, calling and contacts. Malicious dialer apps would take in all that data and use them for unethical purposes.
If this doesn’t work, try rebooting or restarting your phone. The final option is of course a Factory reset. But as you know, factory resetting deletes all your data from your phone. Hence, keep a backup of your data first if you’re going for this ultimate option. Always use genuine Qualcomm Drivers.
Conclusion
Hence, what we conclude is that, com.qualcomm.qcrilmsgtunnel is a built in app present in Qualcomm powered devices. It’s related to your stock phone dialer that deals with calls and messaging stuffs. Force stopping or clearing its data would lead to nothing because it would regenerate again. You also cannot uninstall it if your android device is not rooted. Nonetheless, it is advised not to mess with it. If it’s there, keep it. So, Uninstalling it may give rise to other unruly errors like dialer or messaging app crashing. We have also discussed about the 2016 security breach in Qualcomm devices that use Android 5.1 or lower. Hence, if you are one of them, consider upgrading your device as soon as possible. In a few months, we are going to step into Android 12, so there’s no use being backdated.

I am a tech enthusiast. I have a keen curiosity in Data Science, Machine Learning, Deep Learning and Neural Networks. I have acquired knowledge in Python, SQL, Java, Amazon Web Services (AWS) and IoT (Internet of Things). I have built a couple of ML models and worked on datasets in IBM Watson Studio. Besides, I take great delight in content writing, which makes me come here, as I believe that this is one of the most reliable techniques for sharing one’s skill.


